DEFCON 27 experience & takeaways
August 14, 2019
How I got there
A couple security-minded friends and I had been passing around scholarships & contests we could do to get ourselves a ticket to DEFCON. In particular, WISP had a scholarship available and the Women’s Society of Cyberjutsu had a CTF going on where you could win a ticket. I managed to score a ticket from the CTF and was on my way to attend.
However, a little unplanned, I switched jobs and became Security Engineer later in the Summer. I asked if the company would allow for me to attend on their budget despite it being last minute — and they made it work! Thanks to lovely folks at my current company, the ticket was returned and another woman to was able to attend hacker summer camp. 💪
Preparation
To be honest, I didn’t do much preparation — busy with the new job. ¯\_(ツ)_/¯
While I wasn’t particularly active, some of the friends mentioned earlier joined DEFCON groups and made friends with other folks to hang out and chill. I’m prioritizing this more in coming years since I would have loved to meet have company to discuss things with.
In regards to devices, I’m firmly in the camp of no one going to waste a zero day on me. Sure, I made sure everything was up-to-date and things like bluetooth were turned off, but I wasn’t going to sacrifice convenience and personal safety by leaving my phone at home and/or purchasing a burner(s).
[Day 1 — Aug 8, 2019]
Let me just start this off with: daaaaamn, Vegas hotels are huge. I think I spent a majority of this day just wandering around lost.
Started off with the day going to the Paris hotel in search of the badge line. Whoever managed badge line operations did a wonderful job and getting my badge took minutes. However while I did not to partake in the swag line, I heard that was an entirely different story and people waited hours.
Afterwards, I hopped into one of the lines in the area for a random tech talk. I landed in a talk that discussed how quantum computing affects cryptography. I poked around this topic in college a bit and had some background on what was going on.
Some takeaways: quantum computing is an “if not when” sort of thing but it won’t affect the current state of cryptography for a while.
Today’s hardware is noisy as hell but research into things like quantum annealing is really causing the field to accelerate. Some sort of multiplicative effect around improving hardware as well as optimizations around computing. Also, quantum computing is just a ton of Shrodinger’s cats.
After the talk, I wandered out the room and got lost for a really long time. 🙃 Which was actually fine for the most part since there wasn’t too much going on the first day.
[Day 2 — Aug 9, 2019]
On exiting the hotel, check out what I spotted at the casino. 👀
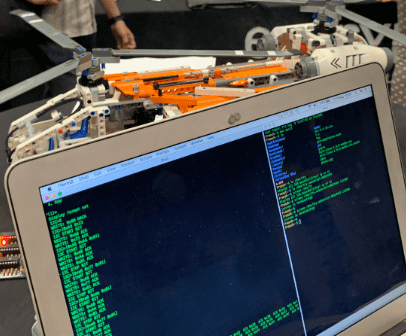
I spent a lot of this day at Aviation Village. The rumor was that you get to learn how to hack airplanes! And it turns out, lego airplanes. Some of the folks running the area mentioned that this sort of work is really similar to what they do everyday but on a much larger scale with many more safety precautions.
For the activity, we (myself and two others) were given a partial set of instructions for to communicate with the bus pirate that was connected to the plane. From that, we were suppose to figure out:
- How to stop the rotors from rotating (on both debug + prod mode)
- Cause the plane to magically smoke
We were able to achieve both goals! We followed low-level commands where we had to poke around with read/write registers and commands to manipulate the device. As someone that mostly works in languages that tend to abstract away many things this was a bit of a refresher on low-level programming. Taking that even further with viewing this from the security standpoint — even more interesting.
[Day 3 — Aug 10, 2019]
I did a lot this day. I woke up at 8:00am and went to sleep at 4:30am the next. That being said, I haven’t been gotten much sleep here in the first place

A coworker pinged my about the Diana Initiative the day before and I decided to attend to briefly get away from the chaos that is DEFCON. I sat in talks on container safety, threat modeling, and privacy research on how women’s health apps leak data.
The last talk was a little enraging since as the saying goes “if the product is free, you’re the product.” In short, all the period trackers that were researched had at least one tracker that sent off your private health information (including information on menstruation cycles, sex, etc.) to somewhere. A stark reminder that there’s still a long way to go for privacy in the tech world.
Heading back to DEFCON, I spent much of the day wandering around various villages (appsec/blue team/iot/recon/etc) and checking out what people were up to. The amount of people participating in contests caught my eye. Contests ranged from the super technical CTF work to making tinfoil hats. I didn’t participate in any contests but I’ll try to see what I can do in the future!
Shout out to whoever designed the area around the scavenger hunt. There was an dark moody futuristic retro sorta vibe going on and it was a beautiful representation of what hacker culture could be. Check out this mannequin from the area, iconic.
One thing I didn’t realize til this day was how fast certain places fill up. There was a talk a talk on 0day hunting/RCE in webapps in the Appsec village that I wanted to attend. I got to the general hotel area a few minutes before it started but saw that there was a giant line of attendees with the same idea. Eventually I made it in the room but had missed a good portion of the talk and had trouble seeing above people’s heads.
The demo talk was rather interesting, it intersects with what I do in the frontend world. The speakers had an open source project on “Shadow Workers” where basically some entity turns service workers rogue. Service workers are a browser-level API that runs scripts in the background — separate from the web page. For example, periodic background sync, push notifications, and offline experiences. Service workers are a farely recent development in the frontend world where they really started becoming popular last year (2018).
Afterwards, I had two Skytalks on my schedule. One I got into and the other I didn’t.
Lesson learned: If there’s a talk you’re really interested in, chances are, others are too! Get there early so you can get a good seat and give the speaker your full attention.
Skytalks are rather interesting. While the official talks are recorded and released, Skytalks are not. Attendees are not allowed to record/take pictures and if you’re seen with a device in hard, you’re kicked from the talk.
I won’t speak much to the talk in particular but it discussed SESTA/FOSTA and the opioid epidemic and how recent legislation is chopping away at Section 230 of the Communications Decency Act which is considered ‘the most important law protecting internet speech’. This has already resulted in increased deaths in already vulnerable populations — a somber topic to walk away. As security professionals we’re taught to ensure confidentiality, integrity, and availability. Recent legislation endangers that and we must pay attention to what’s going on in the world to ensure digital rights.
Nearing the end of the day, I headed out to H1-702, a HackerOne live-hacking event. It was the last day and I had a couple bug bounty friends competing in it. At the end of day and a live hacking event, the organizers throw a “Show and Tell” on the most interesting vulnerabilities found on the particular target. Super interesting to see people’s thought processes around hacking.
[Day 4 — Aug 11, 2019]
Last day of DEFCON!
I spent this day at a SSRF talk, wandering around with friends & new acquaintances, and vegging out at the closing ceremony
The SSRF talk was an official talk should be available to watch…somewhere. The most interesting part for me was discussion around using DNS rebinding to get around same origin policy. The speakers also wrote a tool to make rebinding attacks easy.
The closing ceremony was nice. It’s really interesting to hear how DEFCON has changed through the years and what interesting stats/events happened this year. And to toot my own horn, I was briefly reminded about how the security world needs to work a bit on user experience and accessibility.
While my photo is blurry, this slide was up for a while. Two things to point out here are:
- Colors that are suppose to portray meaning but are inaccessible (red-green + contrast between panels)
- Text that is difficult to read due to size despite having plenty of whitespace around it
Some thoughts & takeaways
- Vegas hotels are a dark pattern and the sleep deprivation does not help. Plan time between talks especially if you have to walk between hotels. During the closing ceremony, the organizers mentioned something about it being held in a convention center next year.
- I think it would’ve been really helpful if I took some time after talks absorbing what just happened. I’m writing this a few days after the conference and I’m sure I’m forgetting plenty.
- Allowing yourself to wander is nice — I stumbled upon a lot of cool things I wouldn’t have otherwise!
- Make a schedule of events your interested in plus backup events if the thing you want to go to fills up.
- Meeting people is as useful and fun as the educational content.
All in all, DEFCON has been my favorite conference to date and I look forward to attending again! 😃